One viable option for overall strengthening of an organisations security posture is to complement the Essential Eight strategies with the internationally adopted and proven NIST Cyber Security Framework.
This framework was created by the US National Institute of Standards and Technology in conjunction with the commercial sector and is based on existing standards, governance, and best practices to reduce cyber attacks.
NIST Cyber Security Framework helps organisations understand their cyber security risks, threats, vulnerabilities and impacts by using customised measures to better respond and recover from a cyber attack.
Where the Essential Eight helps harden Microsoft Windows-based internet-connected networks, devices, and endpoints, the NIST Cyber Security Framework is a set of holistic procedures a business can follow in the likely event an attack occurs.
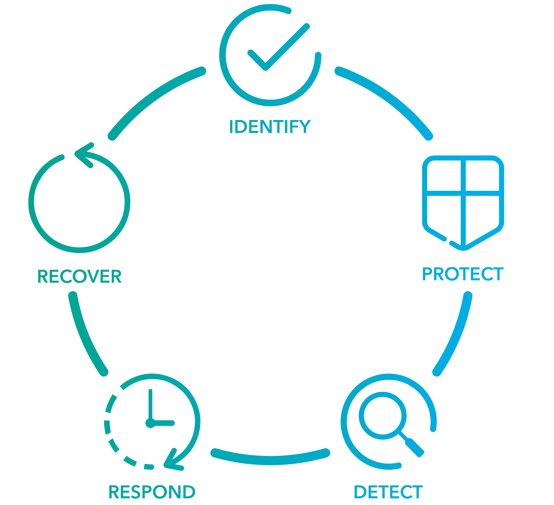
What are the 5 critical functions of the NIST Cyber Security Framework?
Identify
The Identify function lays the groundwork for any cyber security actions. Determining what exists, what risks are associated with those environments, and how it relates to your business goals is crucial to succeeding with the NIST framework. Successfully implementing the Identify function results in a clearly defined cyber security posture. The outcome categories associated with this function include:
- Asset Management identifies personnel, data, devices, systems, and facilities used to achieve core business purposes.
- Business Environment defines the objectives, mission, stakeholders, and general activities of the business.
- Risk Management & Strategy the establishment of constraints, priorities, risk tolerances, which are used to support operational decisions of the business.
- Governance covers policies, procedures, and processes necessary to monitor and manage the legal, risk, regulatory, environmental, and operational requirements of the business.
Protect
The purpose of the Protect function is to develop and implement appropriate safeguards to ensure the security of critical infrastructure. The Protect function supports the ability to limit or contain the impact of a potential cyber event.
NIST takes a proactive approach with multi-factor authentication practices to control access to assets and environments, while employee training reduces the risk of socially engineered breaches caused by human error. The outcome categories associated with this function include:
- Identify Management Authentication & Access Control access to assets and networks should be limited to the least possible privileges. Role-based access should be utilised for facility access, running processes, and team members access to allow just enough access for each process/team member to perform their job functions.
- Awareness & Training easy access to cyber security awareness education. Such training empowers team members to perform their security-based responsibilities in accordance with the policies, procedures, and agreements of the business.
- Data Security management of the company’s sensitive data in accordance with the risk strategy developed to protect the integrity, confidentiality, and availability of vital information.
- Information Protection Processes & Procedure refers to security policies, procedures, and processes maintained and used to manage the protection of the organisation’s data and networks.
- Maintenance performed in accordance with the organisation’s policies and procedures, maintenance also includes any necessary repairs of the industrial control and data components.
- Protective Technology utilise a mixture of manual and automated tools to efficiently ensure optimal security and resilience of your systems and assets.
Detect
The Detect function enables the prompt discovery of cyber security events. This is a critical step in mitigating the damage a breach can cause when swift action is vitally important. The outcome categories associated with this function include:
- Anomalies & Events anomalous activity is detected in a timely manner and the potential impact of events is understood. Determining the definition of “detection in a timely manner,” according to any relevant regulations or compliance obligations.
- Security Continuous Monitoring monitoring your assets and information in real-time, or at defined intervals, allows you to identify cyber security events and to ensure the effectiveness of protective measures for your network.
- Detection Processes proper maintenance of detection systems to ensure their readiness at all times to reliably provide awareness of detected anomalies.
Respond
This function supports the ability to contain the negative impact of any type of cyber security incident. Response covers all activities that you may use to act once a cyber security incident is detected. To do this, your organisation must create a detailed response plan and analyse the effectiveness of your response following a cyber incident. The outcome categories associated with this function include:
- Communications response activities regarding communications between your organisation and your internal and external stakeholders. There are instances which may include communicating with law enforcement depending upon the sensitive data your organisation is holding.
- Mitigations activities performed to prevent the expansion of a cyber security event while also mitigating its effects and neutralising the event.
- Improvements each time an organisation works through response activities, there are new opportunities to strengthen the process by incorporating lessons learned through detection and response. Your team should review what didn't work and update your response plan accordingly.
- Response Planning allows for timely response to detected cyber security events by well-maintained and properly executed processes and procedures.
- Analysis reviews done during response activities to ensure the correct process is followed and support recovery activities.
Recover
Getting back to business as usual is a top priority for any organisation after a breach. To streamline and speed up recovery, it’s crucial to develop a plan before it's required. This function offers a chance to identify the best activities for organisational resilience. It aims to restore capabilities and services that were impaired because of a cyber security incident. This entails recovering data that was lost, restoring capacities that were impaired, and ensuring everything is functioning as intended. The outcome categories associated with this function include:
- Recovery Planning organise recovery processes and procedures according to priority. The actions that are most critical to protecting systems and assets should be placed at the beginning of the plan. During the recovery, your team should be able move from highest priority down the list to quickly accomplish tasks.
- Improvements after the systems are running again, your organisation should review the event and take note of important lessons learned in the process. The recovery plan should then be updated to reflect what you’ve learned.
- Governance covers policies, procedures, and processes necessary to monitor and manage the legal, risk, regulatory, environmental, and operational requirements after a cyber incident.
- Communications in order to restore activities, it’s important to coordinate with internal and external parties. Such parties may include internet service providers, victims, vendors, stakeholders and law enforcement.
How does NIST complement the Essential Eight?
The Essential Eight describes the strategies to advance an organisation's security posture to higher maturity levels. However, the Essential Eight does not factor in the unique IT security requirements and set-up of all organisations, and is only applicable to Windows devices, whereas NIST is a framework based on identification and response protocols.
While it is possible to complement the Essential Eight with other security measures unique to different operational environments, by mapping it with the broader, holistic NIST Cyber Security Framework, a business gains greater clarity on how the Essential Eight standards fit within the bigger security picture. This allows an organisation to better identify possible shortfalls in their existing cyber security set-up.
At Systima, every service we offer is aligned with the Essential Eight and NIST framework. We help create a roadmap for our clients to improve upon their cyber posture and mitigate the risk of an attack. Through these standards and frameworks, we show you how to detect an attack and how to proactively look for malicious actors in your network, whilst determining how long they have been there for. We help formulate an incident management, crisis management and communication plan because after a cyber incident, reassuring your customers and stakeholders is crucial to avoid reputational damage.
The closer a business follows The Essential Eight and NIST Cyber Security Framework, the less likely they will succumb to a breach, and the more effectively they will respond and recover in the likely event of an attack.
Chat to us today about how we can help analyse your current procedures, policies and tools, and build out a cyber security program best suited for you and your business.
Contact Us Today