In 2022, trusted Australian brands like Optus and Medibank have fallen prey to data breaches bringing reputational damage and a ripple effect that many Australians are still feeling today.
For those lagging behind after the digital transformation in the wake of the COVID-19 pandemic, it can be difficult to feel confident with the looming cyber threatscape. Add in a skills shortage and it can feel almost impossible to escape this uncertainty.
The reality is that cyber incidents are here to stay. It's how we respond to these attacks that will be the test for business leaders.
Haven’t we heard all this before?
The short answer is yes, of course we have. We wouldn’t be doing our job properly if we weren’t continuously beating the cyber security drum. The longer answer is that now there is a set of complementary, standardised, automated, and compliance-focused security frameworks, using smart automation and monitoring tools to help mitigate the threat posed by cyber attack.
Governments around the world are aware of this surge in risk and as a result have developed national cyber security strategies to actively protect their citizens, businesses, and critical infrastructure. One of the forerunning strategies comes from the Australian Cyber Security Centre (ACSC) called the Essential Eight.
What is the Essential Eight?
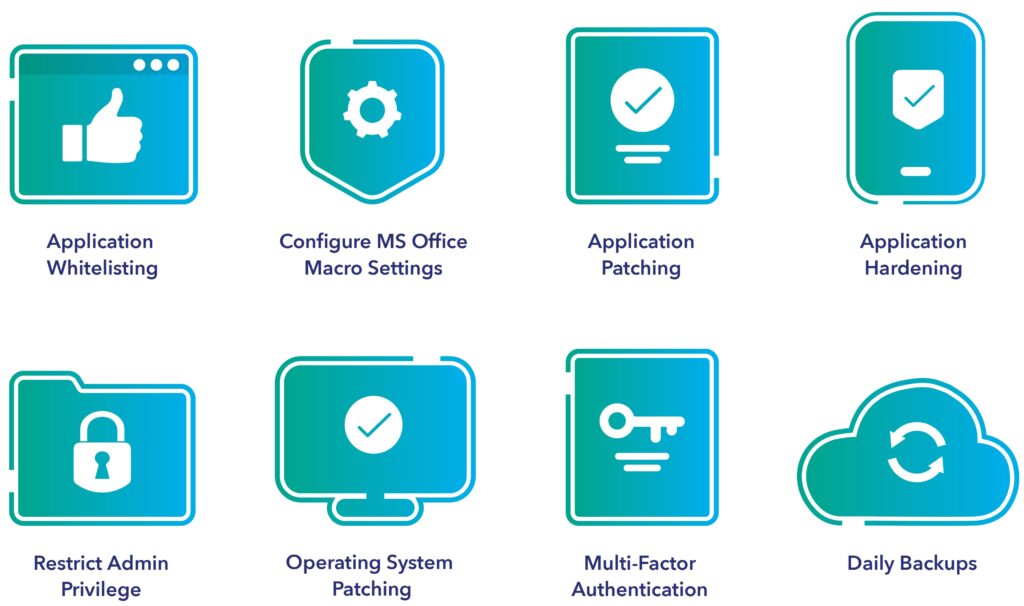
The Essential Eight is a set of practical baseline strategies to help mitigate the risk against cyber attack and is recommended for all businesses, small or large.
It prescribes the eight most effective cyber security mitigation strategies to help harden Microsoft Windows-based internet-connected networks, devices, computers, and endpoints against various cyber threats, and can act as a general checklist for businesses looking to strengthen their security posture.
Application Whitelisting
Protect networks from harmful applications by preventing the execution of malicious programs including .exe, DLL, scripts (e.g., Windows Script Host, PowerShell, and HTA), and installers.
Why? This control is for all non-approved applications (including malicious code) and protects networks from harmful applications.
Application Patching
Identify and repair vulnerabilities in Flash, web browsers, Microsoft Office, Java, and PDF viewers. Patch computers with extreme risk vulnerabilities within 48 hours. Use the latest version of applications.
Why? Security vulnerabilities in applications can be used to execute malicious code on networks.
Configuring Microsoft Office Macro Settings
Harden Windows environments by blocking macros from the internet, and only allow vetted macros either in trusted locations with limited write access or digitally signed with a trusted certificate.
Why? Microsoft Office macros, for example, can be used to deliver and execute malicious code on networks.
Application Hardening
Eliminate vulnerabilities and increase security by configuring web browsers to block Flash, ads, and Java on the internet. Disable unnecessary features in Microsoft Office, web browsers, and PDF viewers.
Why? Flash, ads, and Java are popular ways to deliver malicious code on networks. Eliminate these vulnerabilities and increase security.
Restricting Administrative Privileges
Limit access to networks and systems based on duties of your team. Regularly assess the need for privileges. Don’t use privileged accounts for reading email and web browsing.
Why? Admin accounts are the way in for malicious actors. Adversaries use these accounts to gain full access to information and networks.
Operating System Patching
Identify and repair hardware with extreme risk vulnerabilities within 48 hours. Use the latest operating system version. Don’t use unsupported versions.
Why? Security vulnerabilities in operating systems can be used to further the compromise of networks.
Multi-factor Authentication
Add another layer of security including VPNs, RDP, SSH, and other remote access, and for all staff when they perform a privileged action or access an important data repository.
Why? Stronger authentication adds another layer of security and makes it harder for adversaries to access sensitive information.
Daily Backups
Ensure uninfected critical data is available after a breach with daily back-ups of important new or changed data, software, and configuration settings, stored disconnected. Retained for at least three months. Test restoration initially, annually, and when IT infrastructure changes.
Why? To ensure uninfected critical data is available after a breach.
How do the Essential Eight Maturity Levels work?
To assist business in implementing the Essential Eight, four maturity levels have been defined by the ACSC. Each maturity level is based on mitigating the tools, tactics, techniques, and procedures hackers have at their disposal, also known as adversary tradecraft.
The Essential Eight’s maturity model can offer a simple way to benchmark an organisation's preparedness for a cyber attack and show them the best path forward.
Maturity Level Zero
This maturity level signifies that there are weaknesses in an organisations overall cyber security posture. If an attack occurs, these weaknesses will be exploited resulting in the compromise of confidential data, or significant loss of systems and data.
Maturity Level One
The focus of this maturity level is hackers who are looking for any victim rather than a specific victim. They will opportunistically seek out common weaknesses in many targets by casting their net wide rather than investing heavily in gaining access to one specific target.
Maturity Level Two
The focus of this maturity level is hackers operating with a modest tradecraft set-up. These adversaries are willing to invest more time in a specific target and, perhaps more importantly, in the effectiveness of the tools they use to gain access to networks.
Maturity Level Three
The focus of this maturity level is adversaries who are more adaptive and much less reliant on public tools and techniques. These adversaries can exploit the opportunities provided by weaknesses in their target’s cyber security posture, such as the existence of older software or inadequate logging and monitoring. Adversaries are able to extend their access, evading detection whilst solidifying their presence in an organisation's networks.
What if business leaders fail to comply with the Essential Eight?
The Essential Eight is the Australian Signals Directorate set of best practices, endorsed by the Australian government. Cyber insurance questionnaires are primarily modelled on these set of standards. The less aligned your business is with the Essential Eight, the more risk you take on, and therefore, the more expensive covering your business will become. Furthermore, the Australian government has recently passed legislation to fine companies up to $50 million for data breaches. Business leaders who fail to align their business with these government endorsed set of standards risk exposing their business to the financial and reputational repercussions a cyber attack brings.
At Systima we do a gap analysis on your current procedures, policies and tools. Then we create a roadmap that aligns your business with the Essential Eight standards, ultimately improving your security posture and mitigating the risk of cyber attack.
If implemented to a satisfactory level, the Essential Eight will significantly reduce the very real risk of being breached. However, cyber security is not a set and forget process, it’s an ongoing review of your security posture to ensure your set-up can respond to an ever-changing threatscape.
Chat to us today about how we can create a cyber security roadmap for your business.
Contact Us TodayIn our next blog, we explore how the NIST Cyber Security Framework complements the Essential Eight when implemented together.